The moment that you realize that you clicked the wrong link.
When that newish employee sheepishly comes into your office because he can’t log into his computer anymore.
That time between your desktop showing nothing but gibberish and when you get the data ransom demand.
The sophistication and sheer volume of malware, phishing and hacking attempts made every minute, even to small and medium sized businesses here in the Tampa Bay area, make it almost a certainty that your data will be attacked.
And you simply cannot control when and how your systems will be attacked, or those sinking feelings when what’s described above happens in your office.
What you CAN control is what happens next.
Data Breach Aftermath
One of 2 things will happen after you receive that ransomware demand – and if you’re very lucky you WILL get a demand for money, and not just be at the whim of some destroyer that simply wants you cause harm:
1 You send everyone home and start scrambling to buy bitcoins to bribe your way back to doing business. Count the losses and live with the embarrassment while you do that.
2 You call us, Verified Technologies. (Or your current high quality outsourced IT company) Not because you find us online and think we can help after the fact. Because for the most part, no one can.
But because you have a disaster recovery plan in place.
If you’ve chosen option 2, you’ll be back in business within a few hours. Blissfully unaware of the ins and outs of cryptocurrency and the wait to find out if the hackers will actually free your data once they’re paid.
The Threat to your Data
In 2019 Ransomware attacks cost companies $7.5 BILLION dollars.
And Q3 of 2020 ransomware payments were up 468% vs the same quarter last year.
According to Dato Global, the average cost of downtime is 24 times more expensive than the ransom paid.
So not only are small companies being attacked more and paying more – it STILL makes more financial sense to pay than to fight. Unless of course, you have that Disaster Recovery plan already in place.
What is Ransomware?
Ransomware is a form of malware that encrypts a company or individual’s files.
It can attack an individual desktop and then jump onto the company network and encrypt the company’s entire dataset. Imagine coming into the office one morning and finding all the following completely inaccessible:
- Accounting systems
- CRM
- Local Backup
- Employee files
- Customer files
- Tax records
- Inventory records
- Tax records
- Shipping information
Once this data is also completely unusable the owner will usually be contacted with an offer:
Pay this fairly low amount of money in untraceable cryptocurrency and you will be sent a decryption key that will return your data to you.
Or ignore the payment request and try and rebuild everything from scratch.
That’s why Verified Technologies helps you implement procedures and policies to minimize risk, and backup systems that guarantee a business-preserving short downtime.

How does Ransomware get on My Network?
The most common way this happens is basic phishing.
Hackers aren’t usually targeting you specifically but create and send mass emails with a reasonable link or download file attached to thousands of companies.
You’ve probably seen them:
“This invoice is overdue. Click here to download”
“Here’s the purchase order you were expecting, click here to process order”
“You’re qualified to receive ______”
Here’s an example of one of the more obvious phishing attempts:
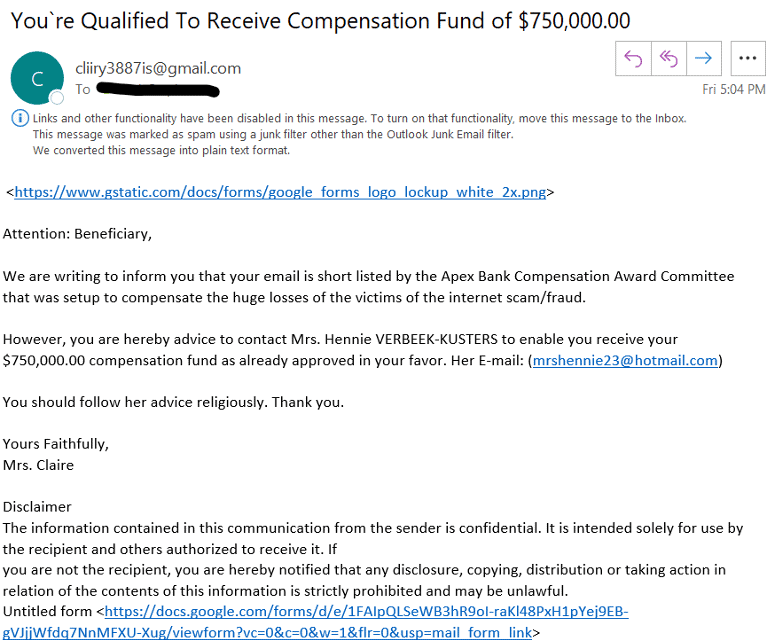
Of course – any and all of the links in this example will lead you to the opportunity to unknowingly install malware onto your system!
Luckily, if you educate your employees well enough these kinds of obvious attempts are fairly simple to avoid.
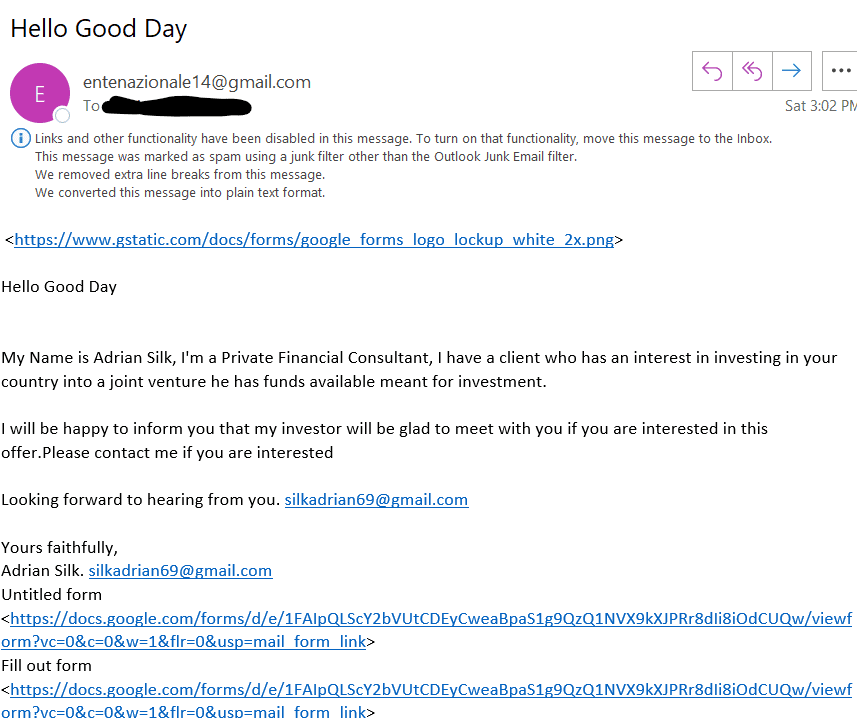
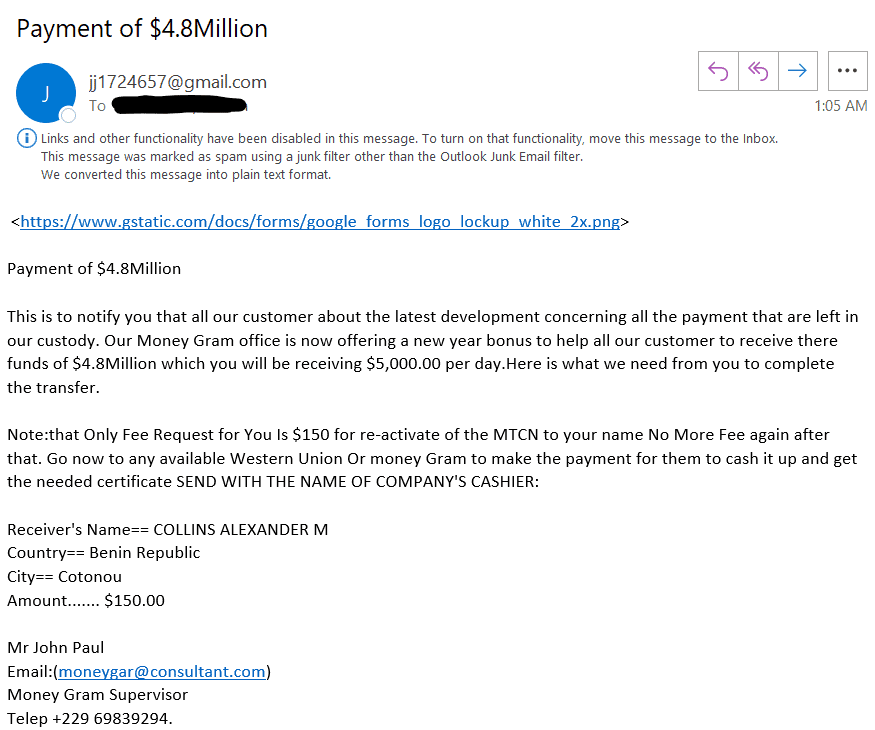
But then comes Social Engineering
A more advanced way to get your employees to download ransomware is by making the emails look more legitimate through “spoofing”.
Spoofing is when the hacker creates a “from” email and signature that you would normally expect to receive and inherently trust.
For example, one Verified Technologies client company had their CEO’s email address spoofed.
In a straight phishing attempt the hacker might simply send an email saying:
“Please read this [link]”
Respectfully,
Your Actual Boss
In a more developed attack, you may get an email from hr@ yourcompany.com asking you to confirm your login and password. Or your social security number and address.
These attacks are much more specific and smart. They’ll come from a familiar-looking email address, and often from someone in a position of authority.
An email from your boss, the business owner, or your HR department is much more likely to be opened and then responded to quickly – without much thought as to its legitimacy.
How to Prevent Data Disaster
Think about all of your employees.
How busy they are.
How many emails they get each day.
The truth is that there’s no way to prevent your staff, and then your company, from falling victim to attacks with 100% certainty.
Good policies and procedures. Strong passwords. A suite of sophisticated malware and virus protection systems definitely reduces the risk, but nothing is guaranteed.
Here’s some great information about creating passwords from CNET
In order for Disaster to be avoided, the only sure thing that you can do is have fully protected, ready to deploy backups in place.
Comprehensive backup, recovery, and reporting for multiple environments.
A SINGLE Business Continuity platform supporting.
All from a company that knows you and your business




